Nacha Rule Changes – What You Need to Know for 2026
Nacha is requiring the standardized use of specific transaction descriptions for ACH entries:
- ACH credits related to wages: Must use the description "PAYROLL"
- ACH debits related to e-commerce purchases: Must use the description "PURCHASE"
This rule applies to all commercial originators initiating these types of transactions. The goal is to improve identification, reconciliation, and transparency for both originators and recipients.
Action Required for West Shore Bank ACH Originators
- Establish and Implement Risk-Based Procedures: As an Originator, you are responsible for establishing and following processes designed to detect outgoing ACH Entries that could be unauthorized or initiated under false pretenses.
- Annual Review: Review your processes and procedures at least annually and update them as needed to address changing fraud risks.
- Risk-Based Approach: Conduct a risk assessment to distinguish high-risk from low-risk transactions and implement monitoring measures accordingly. This approach helps you allocate resources where the risk is greatest.
Who does this new rule apply to?
This rule applies to all West Shore Bank business customers who originate ACH files. Any business, government entity, or organization that initiates ACH transactions (such as payroll, vendor payments, or collections of customer payments) is considered a non-consumer Originator.
Is West Shore Bank the only bank affected by the rule?
No, this was a mandated rule change by Nacha affecting all financial institutions that have business customers who originate ACH payments.
When do I need to comply with the new rule?
The NACHA deadline for implementing these essential fraud monitoring processes is March 20, 2026.
To manage this change efficiently, all new business customers who sign up for ACH Origination on or after January 1, 2026, will be asked to implement the new requirements as part of their initial setup. All existing customers must ensure these new requirements are fully implemented by the March 20, 2026, deadline.
West Shore Bank will incorporate the review of your new fraud monitoring processes into your established annual ACH review process as part of the security Best Practice Checklist, unless changes to your ACH service require an earlier review.
What does “false pretenses” mean and why does it matter?
Nacha introduced the term “false pretenses” to describe fraud where someone misrepresents their identity, authority, or account ownership—common in scams like Business Email Compromise or vendor impersonation.
- Business Email Compromise (BEC): A fraudster impersonates an executive or vendor via email to instruct an ACH payment to a fraudulent account
- Impersonation: A fraudster calls or emails to trick an employee into changing payment information for a legitimate vendor or employee
Banks can now return ACH payments they believe were obtained through deception using return code R17. This change helps reduce fraud and improve the chances of recovering funds.
How can you protect yourself?
- Verify requests: Always confirm payment instructions using trusted contact information.
- Be cautious of urgency: Scammers often pressure you to act quickly.
- Watch for red flags: Unusual email addresses, poor grammar, or sudden changes in payment details.
- Secure your accounts: Use strong passwords and two-factor authentication.
- Stay informed: Train your team and review account activity regularly.
If you suspect fraud, contact your treasury management team immediately at treasurycustomerservice@westshorebank.com or 231-845-3580.
What other types of threats should I consider when implementing my fraud monitoring processes?
Effective fraud monitoring processes must be layered and tailored to your business. What you monitor should depend on your specific ACH transactions (e.g., payroll vs. vendor vs. collection of customer payments).
In addition to the rule’s requirements, your program should consider:
- Unauthorized Withdrawals: How can you prevent external parties from pulling money without permission?
- Internal Misconduct: How can you prevent misuse of payment authority by employees?
- Compromised Credentials: How can you protect your internal systems used for managing payment information and activity?
- Change Request Fraud: How can you verify the authenticity of payment instruction changes?
Does West Shore Bank require me to use a specific software system?
No. The rule is principles-based, not prescriptive. It requires you to implement risk-based processes and procedures that are effective for your specific business. This can include:
- Manual, documented internal controls
- Utilization of new features in your accounting or payroll software
- Adoption of a third-party fraud monitoring solution
Does this rule change my liability for ACH fraud losses?
No. This rule is a compliance standard for Originators, Third-Party Senders, and all Financial Institutions. It establishes a requirement for all Originators to have active, risk-based fraud monitoring. It does not change the fundamental allocation of liability for fraud under existing law, but it does require you to strengthen your controls to mitigate these risks.
What are some examples of risk-based processes for my business?
Your ACH fraud monitoring should fit your business. Processes must be tailored to your structure, payment volume, and specific risks. The examples below are for guidance only—they’re a starting point, not a full checklist. Your approach may include a mix of procedural and technical controls:
- Dual Authorization/Segregation of Duties: Requiring at least two separate individuals to authorize high-dollar payments or ACH files. No single person should be able to create, approve, and release payment
- Out-of-Band Verification: When receiving an email request for a bank account change (vendor or employee), verifying the change via a trusted secondary channel (e.g., a phone call to a known number on file, not the number listed in the suspicious email)
- System Controls and Anomaly Detection: Utilizing your internal accounting or payment systems to automatically flag or alert you to unusual activity, such as:
- Payments to a new vendor that exceeds a set dollar threshold
- Sudden increases in transaction volume or amount outside of normal business patterns
- Unusual payment destinations (e.g., high-risk geographical locations)
- Pre-Payment Account Validation: Utilizing ACH prenotes (zero-dollar verification) or third-party validation services to confirm the existence and ownership of a new vendor’s or employee’s bank account before the first live payment is initiated
- Strong Access Controls (MFA): Limiting the number of employees who have access to your ACH origination system (e.g., payroll or accounts payable software) and enforcing Multi-Factor Authentication (MFA) for all users to protect against compromised login credentials
- Dedicated Payment Workstations: Restricting the computers used to initiate or approve ACH payments from being used for high-risk activities like opening external email attachments or general web browsing
- Formal Fraud Incident Response Plan: Maintain a clear plan outlining immediate actions if fraud occurs, including who to contact at West Shore Bank and internal steps to contain the risk.
- Mandatory, Continuous Employee Training: Provide regular (e.g., quarterly) training for all payment staff to spot, question, and independently verify suspicious requests—an essential defense against social engineering.
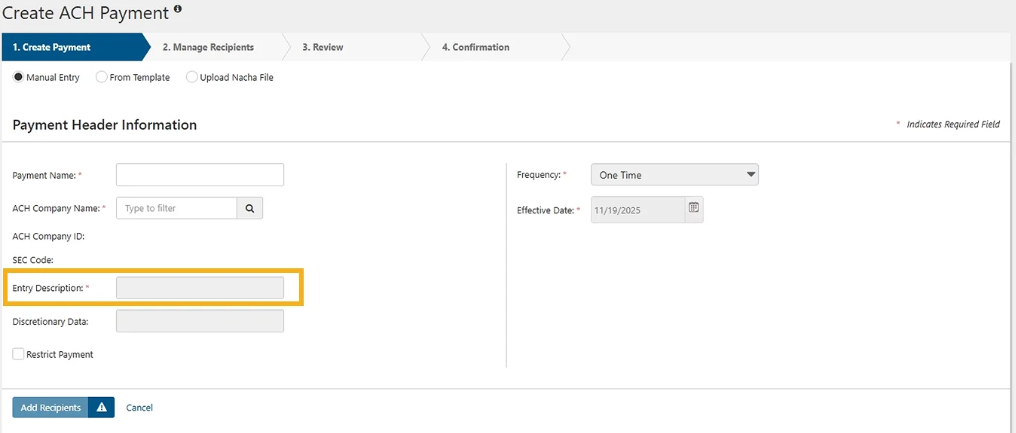
- For New ACH Payments: All newly created ACH payments, populate the Entry Description field.
- For existing ACH Template: Update your payroll templates to include "PAYROLL" in the Entry Description field for all relevant payroll credits, and "PURCHASE" for all relevant e-commerce debits.
- Ensure that all ACH credits for wages are labeled with "PAYROLL" in the Entry Description field.
- Ensure that all ACH debits for e-commerce purchases are labeled with "PURCHASE" in the Entry Description field.
- Third-party software: If you use a third-party payroll or accounting software, reach out to them to understand how to implement this change and make sure your systems are updated accordingly.
- File Imports: If you use an import file for ACH transactions, please coordinate with your technical teams or third-party service providers to make necessary updates before the rule takes effect.
Who does this new rule apply to?
This rule applies to all West Shore Bank business customers who originate ACH credits related to wages and ACH debits related to e-commerce purchases.
Is West Shore Bank the only bank affected by the rule?
No, this was a mandated rule change by Nacha affecting all financial institutions that have business customers who originate ACH payments.
When do I need to comply with the new rule?
The NACHA deadline for implementing these entry descriptions is March 20, 2026.
Non-compliance may result in processing delays or other issues. We recommend beginning to review and update your templates and ACH processes as soon as possible to ensure a smooth transition.
